By
- Ben Lutkevich,Site Editor
- Ivy Wigmore
What is an executable file (EXE file)?
An executable file (EXE file) is a computer file that contains an encoded sequence of instructions that the system can execute directly when the user clicks the file icon. Executable files commonly have an EXE file extension, but there are hundreds of other executable file formats.
Some executable file types can run on any compatible system without requiring the existence of another program. These files are considered to pose a high security risk. They include EXE, BAT, COM, CMD, INF, IPA, OSX, PIF, RUN and WSH.
With Windows, EXE is the file extension for an executable file. All EXE files are executable files, but not all executable files are EXE files.
How does an EXE file work?
EXE files are a Windows-specific executable file format. When a user or other event triggers an executable file, the computer runs the code that the file contains.
Executable files contain binary machine code that has been compiled from source code. This low-level code instructs a computer's central processing unit on how to run a program. The processor interprets the machine code and tells the computer's hardware what to do.
Executable files communicate directly with the computer, giving it a set of instructions to run. By contrast, with data files, another program must interpret or parse them before the machine can use them. Data files, or scripts, are written in plaintext.
Users can create executable files in a basic text editor or in an integrated development environment (IDE). If using a text editor, users need a separate compiler to turn the file into machine code. IDEs automate the compilation process. They also usually automatically find syntax errors and highlight different syntax elements.
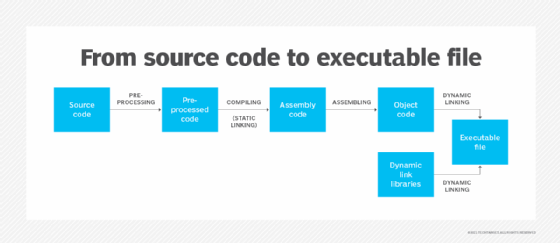
How to run an EXE file
EXE files run when they are opened because opening an EXE file triggers it. This process is different from system to system. The following are two other examples of how executables are triggered:
- In a graphical user interface-based operating system (OS), clicking on the file icon or file name opens and runs the file. For example, in Microsoft Windows, users can double-click the file to run it.
- In a command-line interface-based OS, users enter the file name in the CLI with the proper syntax and press the Enter key to run the file. For example, in Linux or Unix, the user would type a period and forward slash before the file name, so typing ./filename would execute the file called filename.
In some cases, an EXE file can be triggered passively. For example, Windows has AutoPlay and AutoRun features that execute files automatically when a certain event happens. For example, when a USB device is connected, it automatically runs the USB's firmware. Any executables in the Windows startup file will also run automatically when the system boots up.
The EXE file extension is common, but it is specific to executable files on Windows. Mac executable files have the APP extension. To run an EXE file on a Mac OS, users must run the Boot Camp utility or some other virtual machine or emulator that simulates a Windows OS.
Malware concerns with executable file
In some cases, EXE files can contain malware. Malware authors can disguise malicious executable files behind other file extensions.
The characters after the last period in a file name specify the file type. Windows does not always display file extensions, which can make it difficult to know the type of a given file.
For example, a file called trustedfile.pdf.exe may appear to the user as a PDF because, without the extension, the file name would display as filename.pdf. The user would click this, expecting to open a PDF, but it instead triggers an executable containing malicious code, which installs malware on the user's computer.

Looking at the source of an EXE file and whether it arrived in email unsolicited can help users determine if it's safe. If there are doubts about the source, the user can run the file through an antimalware scanner or manually do static analysis on the source code by translating the machine code back to assembly code and analyzing it for malicious functions.
Executable files that deliver malware are a significant cybersecurity threat. Learn how to create a strong cybersecurity plan to defend against executable malware and other cybersecurity threats.
This was last updated in January 2022
Continue Reading About executable file (EXE file)
- 10 common types of malware attacks and how to prevent them
- Researchers use PyInstaller to create stealth malware
- How to use Python for privilege escalation in Windows
- How to use Ghidra for malware analysis, reverse-engineering
- Get started with the Ghidra reverse-engineering framework
Related Terms
- What is machine code (machine language)?
- Machine code, also known as ‘machine language’ or ‘native code,’ is the elemental language of computers. It is read by the ...Seecompletedefinition
- What is natural language processing (NLP)?
- Natural language processing (NLP) is the ability of a computer program to understand human language as it’s spoken and written --...Seecompletedefinition
- What is project planning?
- Project planning is a project management discipline that addresses how to complete a project in a certain time frame, usually ...Seecompletedefinition