Symmetric vs Asymmetric encryption involves key differences: Symmetric encryption uses one key for encryption and decryption, making it faster but requires secure key distribution. Asymmetric encryption uses a pair of keys-public and private-providing enhanced security for key exchanges and digital signatures.
In cybersecurity, encryption is crucial in safeguarding sensitive information or data from unauthorized access. It is a basic technology that commonly employs two different types: symmetric and asymmetric encryption. These methods operate on different principles and offer varying levels of security.
This article discusses two popular encryption schemes, Symmetric and Asymmetric. We will look at the definitions of algorithms and key cryptographic concepts. Later, we will dive into the core part of the discussion, where we compare the two techniques.
Algorithms
An algorithm is a set of instructions for solving data security concerns. An encryption algorithm is a set of mathematical procedures for performing encryption on data. Through such an algorithm, information is transformed from plaintext to ciphertext. This brings us to the concept of cryptography that has long been used in information security in communication systems.
Cryptography
Cryptography is a method of using advanced mathematical principles to store and transmit data in a particular form so that only intended recipients can read and process it. Encryption is a key concept in cryptography – It is a process where a message is encoded, known as ciphertext so that it cannot be read or understood by an eavesdropper. The plain text can be encrypted into ciphertext, which can be sent through a communication channel without the risk of interference. When it reaches the receiver end, the ciphertext is decrypted to the original plain text.
Cryptography Terms
- Encryption: It is the process of locking up information using cryptography. Information locked this way is in unreadable format known as ciphertext.
- Decryption: The process of unlocking the encrypted information using cryptographic techniques.
- Key: A secret like a password used to encrypt and decrypt information. There are a few different types of keys used in cryptography.
- Steganography: It is the science of hiding information within other data, such as an image, audio file, text, etc.
What is Symmetric Encryption?
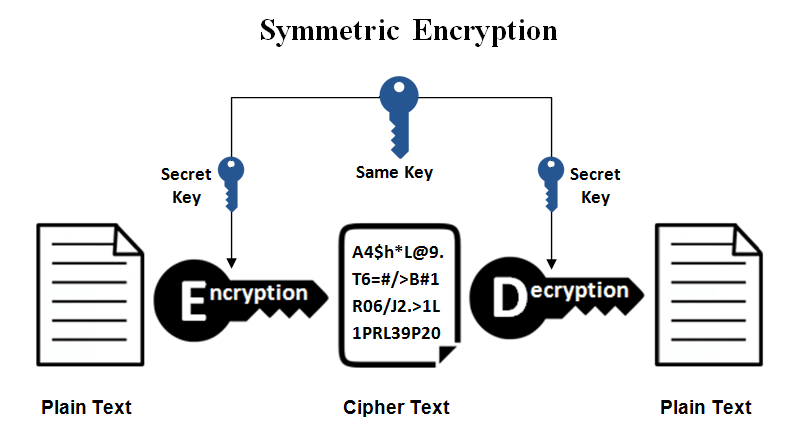
Symmetric encryption is the simplest kind of encryption that involves only one secret key to cipher and decipher information. It is an old and best-known technique. It uses a secret key that can either be a number, a word or a string of random letters. The sender and the recipient should know the secret key used to encrypt and decrypt all the messages. Blowfish, AES, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithms are AES-128, AES-192, and AES-256.
Secure messaging applications such as WhatsApp or Signal are real-life examples of symmetric encryption. Here, the messages are encrypted on the sender’s device using a particular symmetric key. It is then shared with the recipient’s device for decryption and reading.
Symmetric encryption is recommended for real-time communications. It is ideal for industries where data encryption and decryption must be rapid and effective. Here, the key must be kept private to ensure security.
The main disadvantage of symmetric key encryption is that all parties involved must exchange the key used to encrypt the data before they can decrypt it.
Pros and Cons of Symmetric Encryption
Pros
- Faster: Since it’s using a single key for encryption and decryption, it’s faster to execute.
- Identity verification: It uses password authentication as a security purpose to prove the receiver’s identity.
- Easy to execute & manage: Users have only one key for encryption and decryption so it’s easy to execute and manage.
- Efficient for bulk encryption: Its speed makes it well-suited for encrypting large amounts of data, such as files, databases, and backups.
Cons
- Sharing encryption keys securely is a task. It poses as a challenge with a risk of key compromise.
- Symmetric is not that scalable, as sharing keys between many people may not be suitable for various users.
What is Asymmetric Encryption?

Asymmetric encryption, also called public key cryptography, is a relatively new method compared to symmetric encryption. Asymmetric encryption uses two keys: a public key for encrypting and a private key for decrypting.
The public key is openly distributed over the internet. But, a private key is kept secret. Thus, only the recipient who has the corresponding private key can decode the information. This dual-key mechanism enhances security by eliminating the need to share one private key over a network.
Online banking is an example of asymmetric encryption. It is because the browser and bank server establish a secure connection using a public key. The browser encrypts critical information with the bank’s public key. Whereas the bank’s server has a private key. This keeps unauthorized parties from intercepting and stealing financial information. It helps maintain the security of transactions and personal data.
Asymmetric encryption is used in establishing secure connections through protocols like TLS/SSL. Popular asymmetric key encryption algorithm includes EIGamal, RSA, DSA, and Elliptic Curve Cryptography (ECC).
Pros and Cons of Asymmetric Encryption
Pros
- Asymmetric Encryption has two keys, one public and one private, so there’s no problem with distributing keys.
- Again, with a pair of keys, it is not difficult to communicate with multiple parties and that’s how it is more scalable in large networks.
Cons
- Performance: Asymmetric Encryption is slower in performance compared to Symmetric Encryption.
- Hard to understand and execute: Asymmetric Encryption is not that easy to implement and manage due to its large key sizes.
Asymmetric Encryption in Digital Certificates
Asymmetric encryption employs public-key cryptography to secure communication. Digital certificates are fundamental to this process, binding a public key to an entity (individual or organization). Issued by trusted Certificate Authorities (CAs), certificates contain information such as the owner’s identity, the public key, the issuing CA, and a validity period.
During a secure communication session, parties exchange digital certificates. The recipient verifies the certificate’s authenticity using the CA’s public key, ensuring the certificate’s integrity. The sender’s public key, extracted from the verified certificate, is used to encrypt data. Only the holder of the corresponding private key can decrypt the message.
SSL/TLS uses both asymmetric and symmetric encryption – asymmetric during the initial handshake and symmetric for bulk data encryption within the secure session. Quickly look at digitally signed SSL certificates issued by trusted certificate authorities (CAs).
Difference Between Symmetric and Asymmetric Encryption
Asymmetric encryption was introduced to complement the inherent problem of the need to share the key in symmetric encryption model, eliminating the need to share the key by using a pair of public-private keys. Below table summarizes the key differences between symmetric and asymmetric encryption.
| Key Differences | Symmetric Encryption | Asymmetric Encryption |
| Size of cipher text | Smaller cipher text compares to original plain text file. | Larger cipher text compares to original plain text file. |
| Data size | Used to transmit big data. | Used to transmit small data. |
| Resource Utilization | Symmetric key encryption works on low usage of resources. | Asymmetric encryption requires high consumption of resources. |
| Key Lengths | 128 or 256-bit key size. | RSA 2048-bit or higher key size. |
| Security | Less secured due to use a single key for encryption. | Much safer as two keys are involved in encryption and decryption. |
| Number of keys | Symmetric Encryption uses a single key for encryption and decryption. | Asymmetric Encryption uses two keys for encryption and decryption |
| Techniques | It is an old technique. | It is a modern encryption technique. |
| Confidentiality | A single key for encryption and decryption has chances of key compromise. | Two keys separately made for encryption and decryption that removes the need to share a key. |
| Speed | Symmetric encryption is fast technique | Asymmetric encryption is slower in terms of speed. |
| Algorithms | RC4, AES, DES, 3DES, and QUAD. | RSA, Diffie-Hellman, ECC algorithms. |
Conclusion
When it comes to encryption, the latest schemes may not necessarily be the best fit. Consider factors like security requirements, data size, and processing power. Both symmetric and asymmetric encryption have their unique strengths and weaknesses. Symmetric encryption offers speed and efficiency for large data transfers, while asymmetric encryption provides enhanced security for smaller data or key exchange. One must always use the encryption algorithm that is right for the task at hand.
As cryptography takes a new shift, new algorithms are being developed in a bid to catch up with the eavesdroppers and secure information to enhance confidentiality. Hackers are bound to make it tough for experts in the coming years, thus expect more from the cryptographic community!