JWT decoder
Use this tool to confirm your JWT is being generated with the metadata and claims you expect, or to examine JWTs other systems are creating to discover their properties.
Below is a sample JWT you can copy and paste into the decoder to try it out.
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE0ODUxNDA5ODQsImlhdCI6MTQ4NTEzNzM4NCwiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIyOWFjMGMxOC0wYjRhLTQyY2YtODJmYy0wM2Q1NzAzMThhMWQiLCJhcHBsaWNhdGlvbklkIjoiNzkxMDM3MzQtOTdhYi00ZDFhLWFmMzctZTAwNmQwNWQyOTUyIiwicm9sZXMiOltdfQ.Mp0Pcwsz5VECK11Kf2ZZNF_SMKu5CgBeLN9ZOP04kZoWhat is a JWT?
JSON Web Tokens (JWTs) are a widely adopted method for securely transmitting information between systems. They are compact, URL-safe tokens that consist of three parts: a header, a payload, and a signature. JWTs play a crucial role in enabling stateless communication between systems by allowing the exchange of authenticated and trusted information.
One of the key benefits of JWTs is their ability to carry relevant user data in a self-contained format, eliminating the need for constant database or session checks. They are commonly used in modern web applications and APIs due to their simplicity, scalability, and compatibility with various programming languages and frameworks.
JWTs provide a secure and efficient means of verifying the authenticity and integrity of data, making them an indispensable tool in ensuring reliable communication and enabling secure access control in distributed systems.
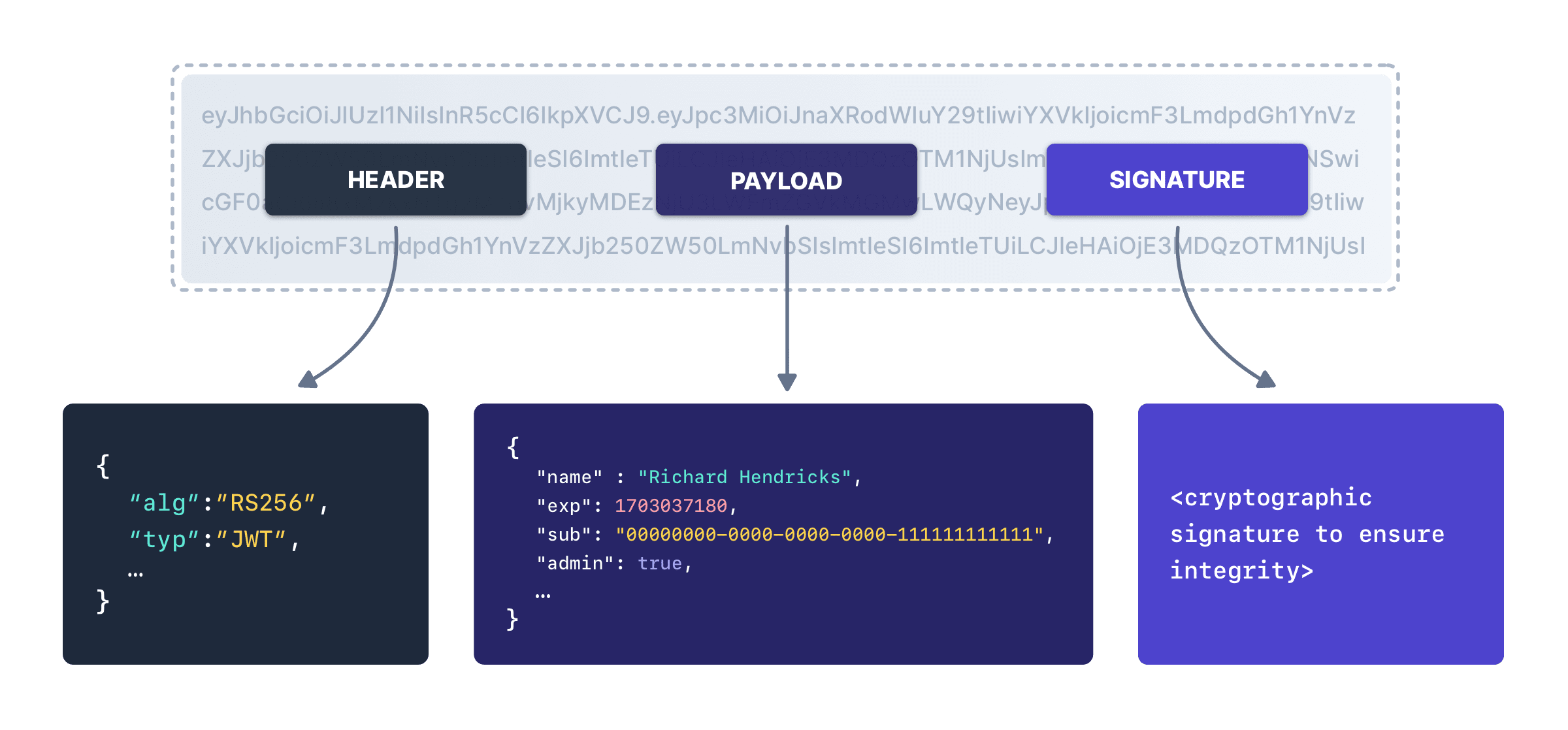
A signed JWT contains these 3 parts:
- A header: which contains metadata, including information about the key used to sign the JWT.
- A body: which is a JSON object with an arbitrary payload; the keys of this JSON object are commonly called “claims”.
- A signature: which is built by performing a cryptographic operation over the header and the body.
These are all Base64 URL encoded so the resulting string is safe to put in HTTP headers, cookies and elsewhere. Every signed JWT lets you verify the integrity of the JWT without contacting the signer.
JWT encoding and decoding
In the encoding and decoding process of a JWT, the algorithm plays a crucial role in ensuring the integrity and authenticity of the token. JWTs utilize cryptographic algorithms to create and verify the signature, which is a critical component of the token.
When encoding a JWT, the algorithm is selected and specified in the header of the token. Common algorithms used for signature generation include HMAC (Hash-based Message Authentication Code) and RSA (Rivest-Shamir-Adleman). The algorithm takes the header and payload of the token, combines them, and applies a secret key or private key to generate a unique signature. This signature is appended to the JWT, creating a tamper-proof token.
During the decoding process, the algorithm specified in the JWT’s header is used to verify the signature. The recipient of the token uses the corresponding secret key or public key associated with the algorithm to validate the signature. By re-computing the signature using the same algorithm, the recipient can compare it with the received signature. If they match, it indicates that the JWT has not been tampered with and that the data it contains can be trusted.
Our online JWT decoder lets you examine the contents of any JWT by pasting it into the Token form field. It’ll automatically decode the values and place the header and body into the respective fields.
The choice of algorithm depends on the specific security requirements and constraints of the system. HMAC algorithms are symmetric, meaning the same secret key is used for both encoding and decoding. RSA algorithms, on the other hand, are asymmetric, utilizing a public key for verification and a private key for signing. The algorithm used should be strong enough to resist attacks and ensure the integrity and confidentiality of the data within the JWT.
JWT best practices
When handling JWTs, it’s crucial to consider JWT security implications, especially because these tokens often hold sensitive data. One of the standard best practices for signed JWTs is to never store sensitive or personally identifiable information (PII) in the payload of a JWT. Since a keyholder can decode JWT data and then read it, storing sensitive information in the payload can expose this data if the JWT is intercepted. Always assume that your JWT can be compromised and only put non-sensitive data into its payload.
In terms of the signing key used with JWTs, it should be kept secret and secure. When using symmetric algorithms like HMAC, the same key is used for signing and verification. This secret key must be kept confidential, and its exposure can lead to severe security risks as an attacker could forge tokens. When using asymmetric algorithms like RSA, a private key signs the token and a public key verifies it. While the public key can be openly shared, the private key must be stored securely. If the private key is compromised, attackers could impersonate the server and issue their own tokens.
Another important security measure is to set short expiration times for your tokens. Long-lived or non-expiring tokens can be a major security risk if they fall into the wrong hands. By setting short expiration times, you limit the time window in which an attacker can misuse a token. Therefore, it’s recommended to implement token refresh strategies that issue new tokens as needed, providing continuous access without the need for re-authentication. It’s also recommended to use HTTPS for all communications involving JWTs to prevent tokens from being intercepted during transmission. Implementing these practices can significantly improve the security of your application when using JWTs.